Ukraine War social media reporting
Ukraine War social media reporting tips and strategies
The Russo-Ukraine war has sparked a flood of misinformation online. There are TikTok users claiming to be inside of Ukraine, posting fake images and videos and encouraging people to donate to their accounts. There are clips from movies and documentaries such as Winter on Fire: Ukraine's Fight for Freedom (2015) on Netflix that are circulating online, claiming to show the war on the ground. Out-of-context photos are being posted all over social media channels, stoking fear, anxiety, and confusion. With all this misinformation and disinformation circulating online – how are journalists and citizens supposed to debunk and verify information independently in such a widespread and fast-moving crisis?
The reality is, they can’t. At least, not without help, tools, and strategies.
The Russian government has long used disinformation as a way to push its political agenda. Putin, a former KGB agent, uses methods of misdirection and deception to create instability and gain strength, according to Western intelligence experts. In fact, U.S. intelligence communities were so certain Russia was going to invade Ukraine that they declassified Putin’s invasion plans in order to try to overcome Russian disinformation weeks prior to the war. But that didn’t deter Putin from invading Ukraine. Russia has built a powerful propaganda machine that weaponizes social media platforms, blogs, websites, and messaging apps. A portion of that propaganda machine was put to the test during the 2016 U.S. presidential election. One of Russia’s coordinated disinformation organizations was called the Internet Research Agency (IRA). And one of its key strategies was to tap into the emotional sentiment of people using social media platforms like Facebook, Twitter, and Instagram in order to help push propaganda. Social media research reveals that users are more likely to spread false or misleading news that upsets or angers them. The Russian government is an expert at manipulating social media platforms’ algorithms in order to get misinformation to go viral online. Although the IRA ceases to exist under its original name now, there are many experts who believe Russian-backed groups are still coordinating propaganda messages online, launching cyberattacks, and conducting other nefarious digital acts in order to push Russia’s agenda in Ukraine.
It’s important to remember that debunking photos and videos is a losing game. There’s too much misinformation online. A more productive mindset is to focus on what you can verify. What do you know to be true based on sources and eyewitness statements? What can you report to the public? What information progresses the story? What is relevant and important information to help citizens make informed decisions? Those questions should guide your social media reporting. And if you are trying to debunk critical footage, then focus on conserving your energy by finding efficient methods of doing so, that way you have time and resources to dedicate to reporting verified information.
The best advice I have for journalists and citizens who are trying to navigate this information space, and this is coming from an expert in social media newsgathering and verification, is to try to rely on verified reporters who are on the ground for primary information. CNN, the New York Times, Washington Post, BBC, and other vetted and reputable news organizations have reporters in Ukraine. However, journalists can’t be everywhere, and that’s why citizen journalists who record user-generated content, also known as UGC, are also incredibly vital in capturing the full scope of what’s happening in Ukraine.
Here’s an example of a newsworthy moment that was captured by an ordinary citizen and uploaded to social media. The video shows a Russian tank driving down a Ukrainian highway. We know this is a Russian tank because it matches earlier reports of Russian tanks that were crossing into Ukrainian territory. While driving down the road, the Russian tank crosses multiple lanes and runs over a pedestrian-controlled vehicle. The video is horrific. And the incident seemed unprovoked.
WARNING SOME READERS MAY FIND THIS CONTENT GRAPHIC AND DISTURBING:
Verify videos by using multiple sources sharing similar footage
So how would we go about verifying this incident? One of the easiest ways to verify whether a video is real or not is by checking whether other social media users are posting videos or photos of the situation from different angles, which is what happened in this case. Since the incident occurred in an urban area, there were several citizens who documented the Russian tank crashing into a pedestrian-controlled car. When it comes to verifying this footage, we can have more confidence that this video not only happened in Ukraine, but also that it took place fairly recently, and was observed by multiple eyewitnesses.
Additionally, there was more footage that appeared on social media channels, like Reddit and Twitter which showed local Ukrainians using their physical strength to try to pull the elderly man out of the wreckage after the incident. Thankfully, the elderly man was alive, according to local reports.
If you’re trying to find similar videos to corroborate a video you’re investigating, then here are some of my tips for how to find that content:
Reverse video search using Google
There’s no easy way to reverse video search online, currently. There’s a lot of time, energy, and processing power that has to be used in order to do that. Therefore, this hack, using Google Images may help you.
First, play the video and capture a screenshot of the video. What you capture in this screenshot is very important. It should be something identifiable like a monument, a visible street sign, a landmark. Try to avoid capturing images of people. Unless they are famous or wearing a uniform, they likely won’t yield many results on Google Images.
Next, upload your screenshot to Google Images using the camera icon.
When you get your results, scan through them to see if you can find anything similar. Or click on the option “More” and navigate to “Videos” to find possible related video content.
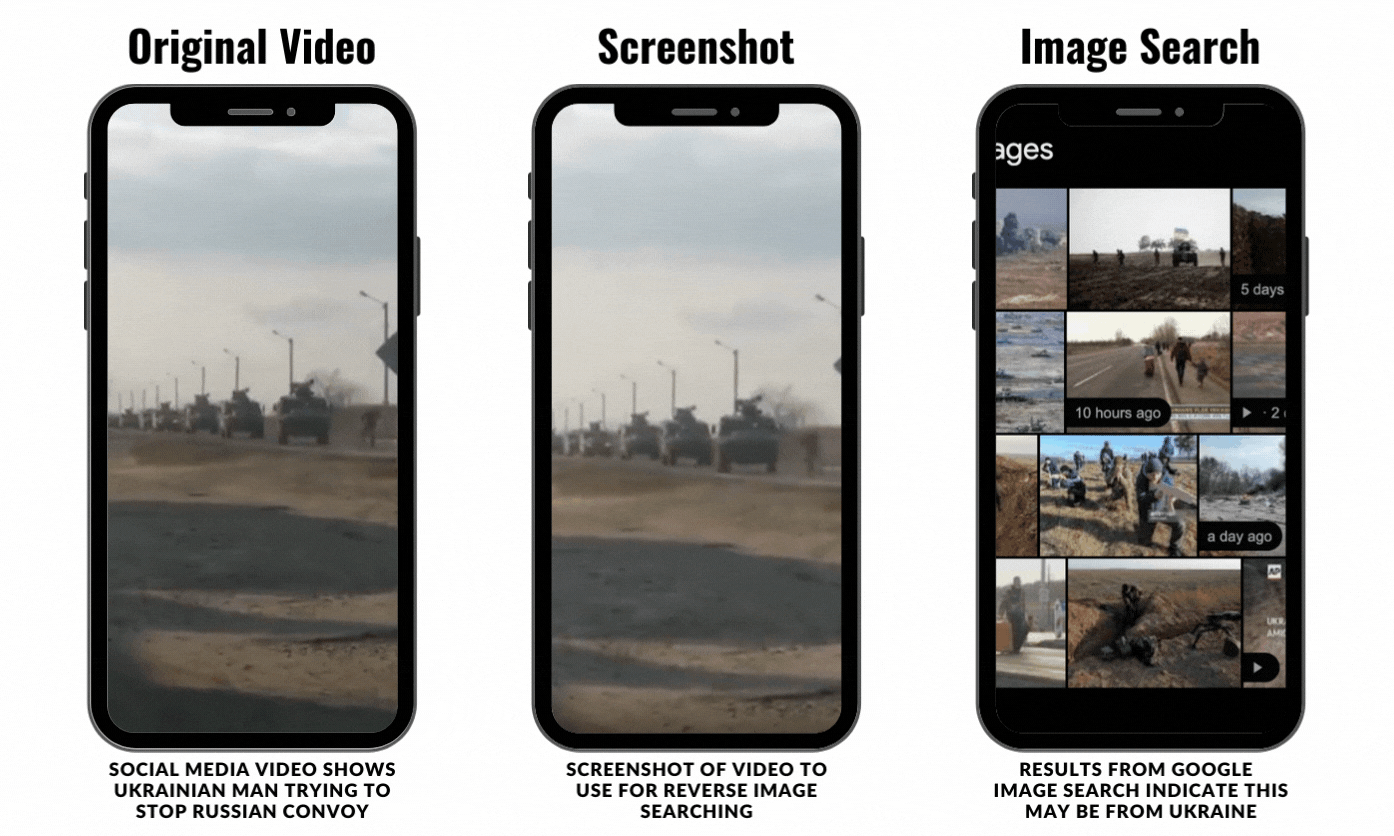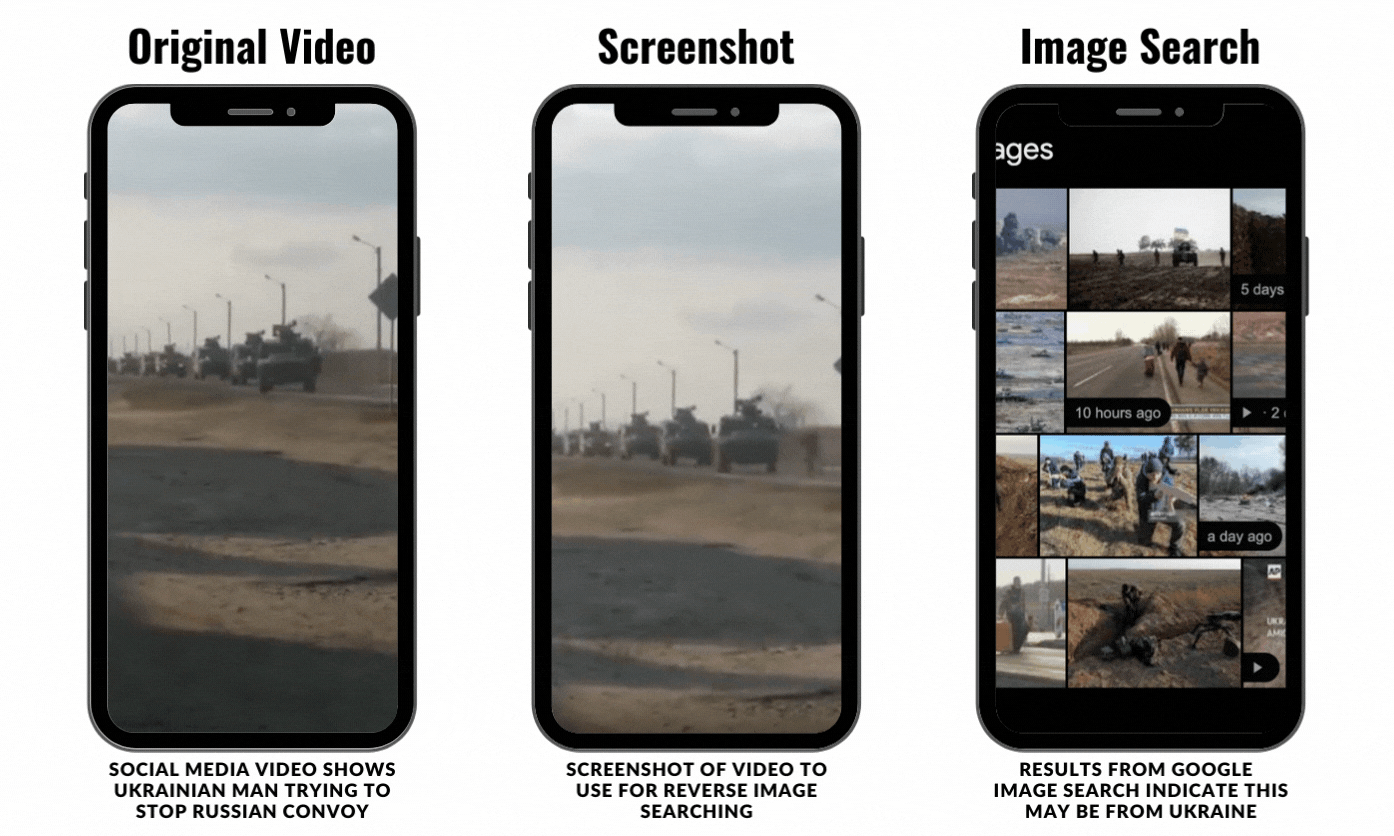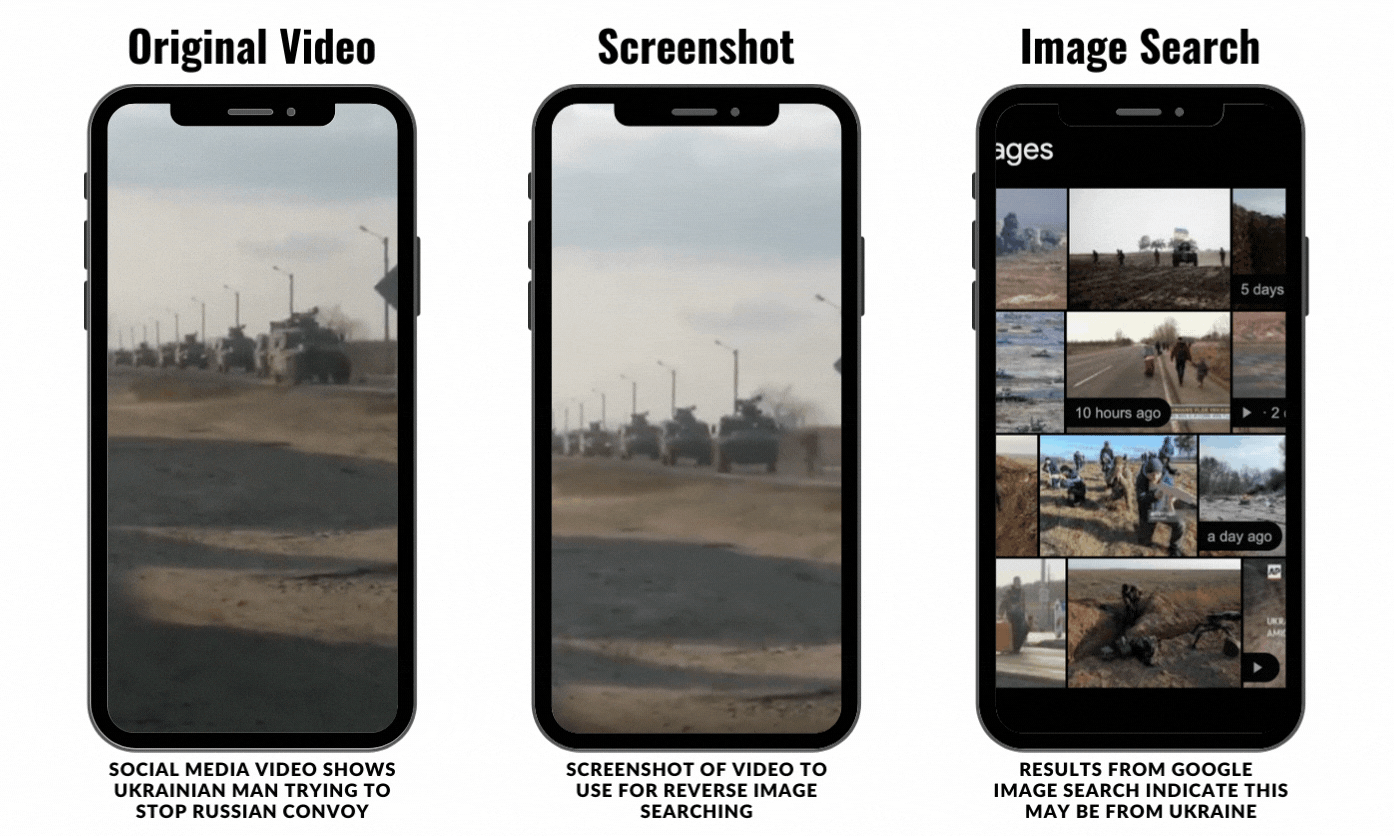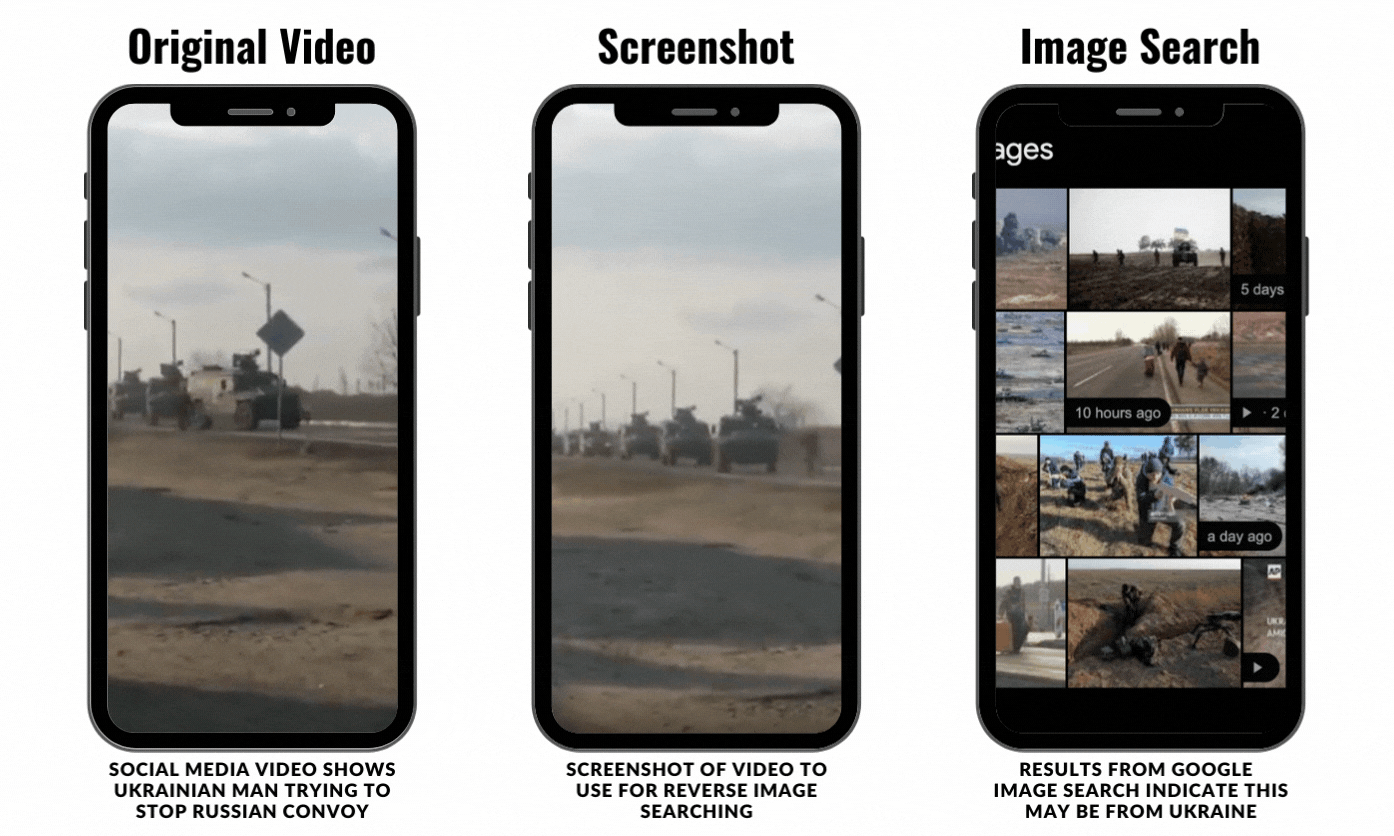
To be clear, this process doesn’t always yield results. The thing about social media investigating is that it is a process of trial and error. For example, the video below was posted around Friday, February 26, and it shows a Ukrainian man running onto a road to stop a Russian convoy from entering Ukraine. It’s a tense video and reminded a lot of people online of the 1989 Tiananmen Square protest and massacre. The video was posted on Twitter by the news outlet HB.
I took a screenshot of the video, which came out a bit grainy, and I uploaded it to Google Images.
Google was able to identify that the image likely was from Ukraine and the Russian invasion, but it wasn’t able to locate the exact video or original source.
How to use Reddit to find similar videos
If the video is going viral and you want to find more like it, you might want to try Reddit. The platform has a very active community of digital sleuths. For example, you could try navigating to r/videos or r/news and looking for posts that match the video you’re investigating. Likely, if the video is going viral somewhere else online, it will be posted on Reddit or sometimes it may have originated from Reddit. What’s interesting about the Reddit community is that some users will post similar videos or add context to news-related content as a way to inform the community. Reading through the comments of posts that match your video may help you discover other videos that are similar too.
For example, the video showing the pedestrian-controlled vehicle being run over by a Russian tank was posted onto Reddit. And then other users replied in the comments of the video to provide other angles and footage showing the same incident. Therefore, corroborating the video.
However, this process might also not also yield results. For example, the video of the Ukrainian man stepping in front of a Russian convoy was uploaded to this subreddit. But if you look through the comments, you don’t find similar images or videos. And that’s likely because it was captured in a rural area, and it’s possible that just one of these videos exists because there weren’t that many people around to document the incident.
Google Earth for verifying Ukraine War photos and videos
But what happens when you don’t have multiple videos of a situation? What do you do? You can try to match the landscape of the video to see if there are similarities with Google Earth, but this is only partially helpful. Because satellite imagery on Google Earth isn’t immediately updated. In fact, some street view images can be a few years old. Since Russian separatists have been in parts of Ukraine since 2014, we can run into problems where location information matches, but those photos or videos may have been captured at another time.
For instance, there was a video circulating online that showed Russian paratroopers floating in the sky as they headed to their destination. The video was circulating throughout TikTok with people claiming Russians were dropping down on Ukraine, however, this video was actually from a training session from earlier in the year. Journalists were able to figure it out because it was still live on Instagram, and the account that posted it (@romanadler123) appeared to have uploaded the video in 2021.
Google Earth does not have historical street view imagery but the feature does exist on Google Maps.
A way to check out old images on Google Maps is to navigate to Google Street View.
From there, depending on the address you’re looking up, a clock icon may display under the address at the top-left of the map, which means historical street view imagery is available for this location.
From there, click the clock to expand the dates to show the imagery that is available.
For example, you can test this process out by looking up this address: 1600 Amphitheatre Pkwy, Mountain View, CA 94043 – this is Google’s main campus. Once you look up the image on Google Maps, you can navigate to street-view and look for the clock that gives you a timeline of historic street-view information.
Google Earth does let you look up some historical satellite imagery. To do this, you will need to download the desktop version of Google Earth. Whenever you use the app, it will default to showing you the current satellite imagery. But to see past satellite images of the same location, you can do the following:
When looking up a location in the search bar, hit enter, and then click on “View.”
Then click on “historical imagery,” which will allow you to select a certain time.
Although these tips may seem simple, they can be extremely powerful. This war already has a lot of disinformation, with the right tools and strategies, you can work on staying informed and safe. And remember, the situation in Ukraine is fast-moving and changing rapidly. If you aren’t sure about the validity of the information you’re watching, then turn to reliable news sources that have journalists on the ground in Ukraine. Stay curious.
How to find EXIF data
See how EXIF data can help you learn more about photos.
When you want to learn more about a photo, sometimes reverse image search might not be enough information to determine the full story of the photo you’re investigating. If you want more information about the location of a photo, the time it was captured, and the make and model of the camera that captured the image – then you’re going to need to dive into the photo’s EXIF data (exchangeable image file).
Why does EXIF data exist?
Although EXIF data may seem spooky to some, or an invasion of privacy to others, it’s actually pretty useful information. For example, have you ever looked at your iPhone and it displays a photo that you captured on a specific day or location and it automatically creates an album for you? Well, if you think about it, you likely didn’t have to manually enter that information for each photo on your phone, right? That’s because EXIF data allows photo-storage programs and services to organize your photos based on date and location, which can make it easier for you to find photos on your computer or phone.
When you share that original photo via email or upload it to certain websites or platforms, the photo’s EXIF data will be attached to it. Many digital security experts believe it is good for consumers to know about EXIF data when they share their photos because consumers may be unaware that they are sharing way more information than they may intend to do.
How do I look up a photo’s EXIF data?
There are a few ways to look up EXIF data, which I will show you in this article. I will also show you a case study for why this technique can really help you determine whether the photo you’re looking at really represents what someone claims it does.
When you take a photo, you’re not just capturing the world around you. You’re also capturing information like date, time, camera model, and other camera settings that are stored as metadata onto your photo. Even information like shutter speed and GPS location are recorded. You don’t need a lot of fancy software to look up this data.
If you’re on a web browser, the website EXIF data viewer is an easy way to upload a photo and look through its metadata. Be mindful of the image size you are looking up though. Web-based EXIF readers usually can’t handle high-resolution photos.
How to check EXIF data on Windows
You can also check EXIF data on your computer, which is my favorite way of doing it. On Windows computers, you just have to right-click on the photo that has been locally downloaded onto your computer and choose “Properties” in the Windows dialogue box. Once you select properties, navigate to “Details.” There, you will find all the camera information you’re looking for – the metadata (e.g. EXIF data).
How to check EXIF data on a Mac
If you’re using a Mac OS, you can also view EXIF data. Once you open a photo on your Mac, you will be in “Preview” mode. From there, click “Tools” in the menu bar. Then click “Show inspector.” This will open a new window where you can select “EXIF.” Here’s a visual breakdown below:
Step 1: Select your photo on your Mac and open it in “Preview”
Step 2: Navigate to “Tools” and select “Show Inspector”
Step 3: Go to “Exif”
Step 4: Based on the device settings of the camera you used to capture your original photo, you will be able to see a lot of information. As you can see here, this photo was captured on July 14, 2021 on an iPhone.
How can journalists use EXIF data for research?
Journalists, citizens, and digital sleuths can use EXIF data to help corroborate an eyewitness account. For example, if someone says they witnessed a stage collapse at a concert and they captured photos of the incident, you could ask them to send you the original photo they captured via text or email. From there, you can look up the EXIF data to see if the photo was really captured in the place, time, date, and with the camera, the eyewitness claims it was captured. This information can help confirm an eyewitness’ story.
Case study of Ghislaine Maxwell
You can also debunk a story or photo with the help of EXIF data. Take the case of Ghislaine Maxwell (who was convicted of sex trafficking in 2021), Jeffrey Epstein’s associate, who in 2019 appeared to be at an In-N-Out Burger soon after reports of Epstein’s death. When I was working at NBC, I got an email to our tips inbox which claimed that Maxwell was not running from the cops or impacted by Epstein’s death, but was instead enjoying her life in sunny California. I thought the email sounded really odd. And I noticed the tipster sent the email with an attached photo.
Before we even start looking at the EXIF data, I noticed the photo had a lot of information in it. We obviously know this is an In-N-Out Burger based on the signage. But where exactly is this restaurant located? Using clues like the buildings behind Maxwell, the billboard, and the bus stop we can make a determination about the exact location using Google Maps and Google Street View.
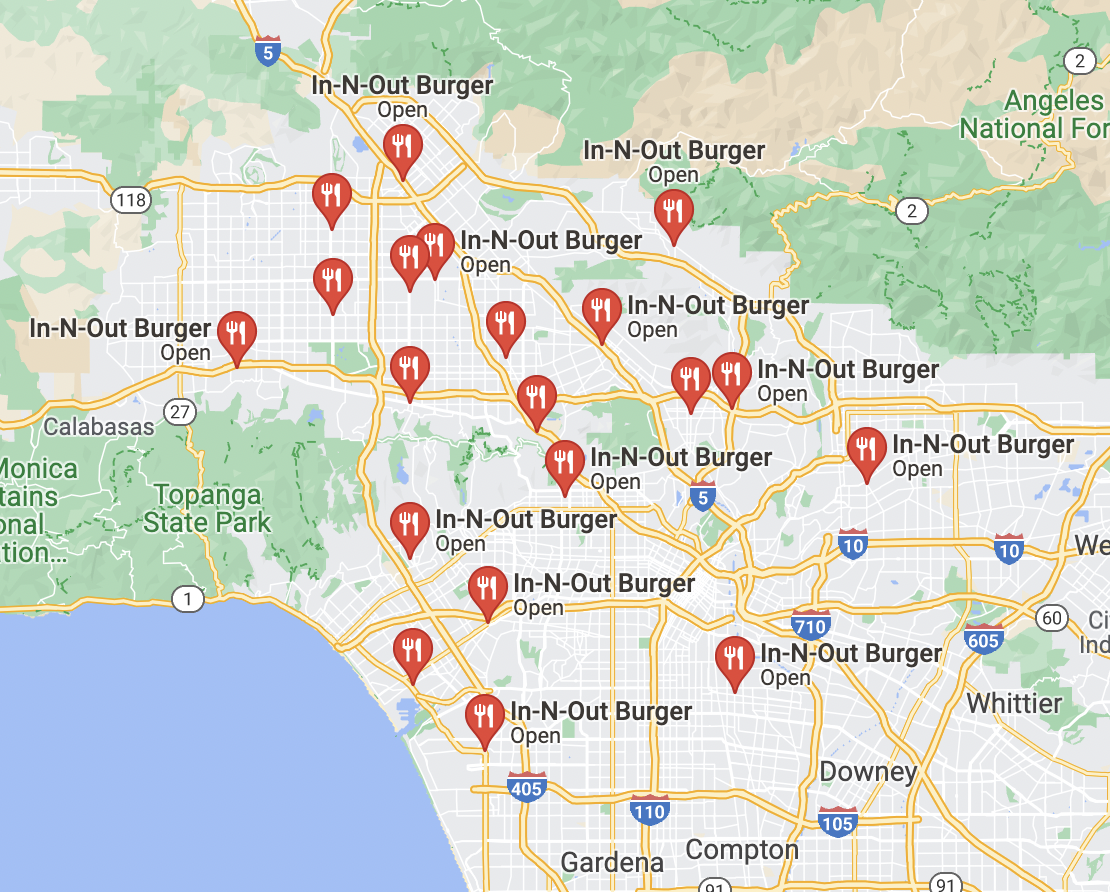
What’s distinctive in this photo in the background is the cannabis billboard. I’ve spent some time in California, so I have seen similar billboards near highways. There are also a lot of buildings clustered around the In-N-Out Burger, which makes me think this photo may have been taken near Los Angeles or in another dense California city area. When you look up all In-N-Out Burgers in Los Angeles in Google Maps, you see that there are about 12 locations.
The next part is a little tedious, but basically, I used Google Street view to look through all the locations until I found one that had the same cannabis billboard in the background. From there, I was able to figure out that the photo was taken at an In-N-Out Burger in Hollywood/Universal City. Not only did the billboard match, but there was also a bus stop and the buildings around the In-N-Out Burger that had green roofing, which matched the tipster’s photo.
So that’s how I was able to establish the location.
Fun fact about bus stops and billboards: Generally, you can call up the business that owns billboards and bus stops because that’s how they attract new clients who may want to advertise with them. When you look at the bus stop in the photo, you see a poster for “Good Boys,” which at the time my former team received this email, was premiering that weekend. The movie was a Universal movie, so my team was able to call the Universal marketing team to ask if the movie was being advertised at that bus stop location. The marketing PR team said no. Which meant that this photo was possibly altered.
Since we figured out the location of this In-N-Out Burger through Google Street View, my former team at NBC was able to figure out the business that owned the bus stop ad spot. We called the number and determined that there wasn’t a movie being advertised there. It was a healthcare ad for a hospital. It was likely then that the person who doctored this photo wanted us to believe it was captured recently by adding the movie poster to the photo.
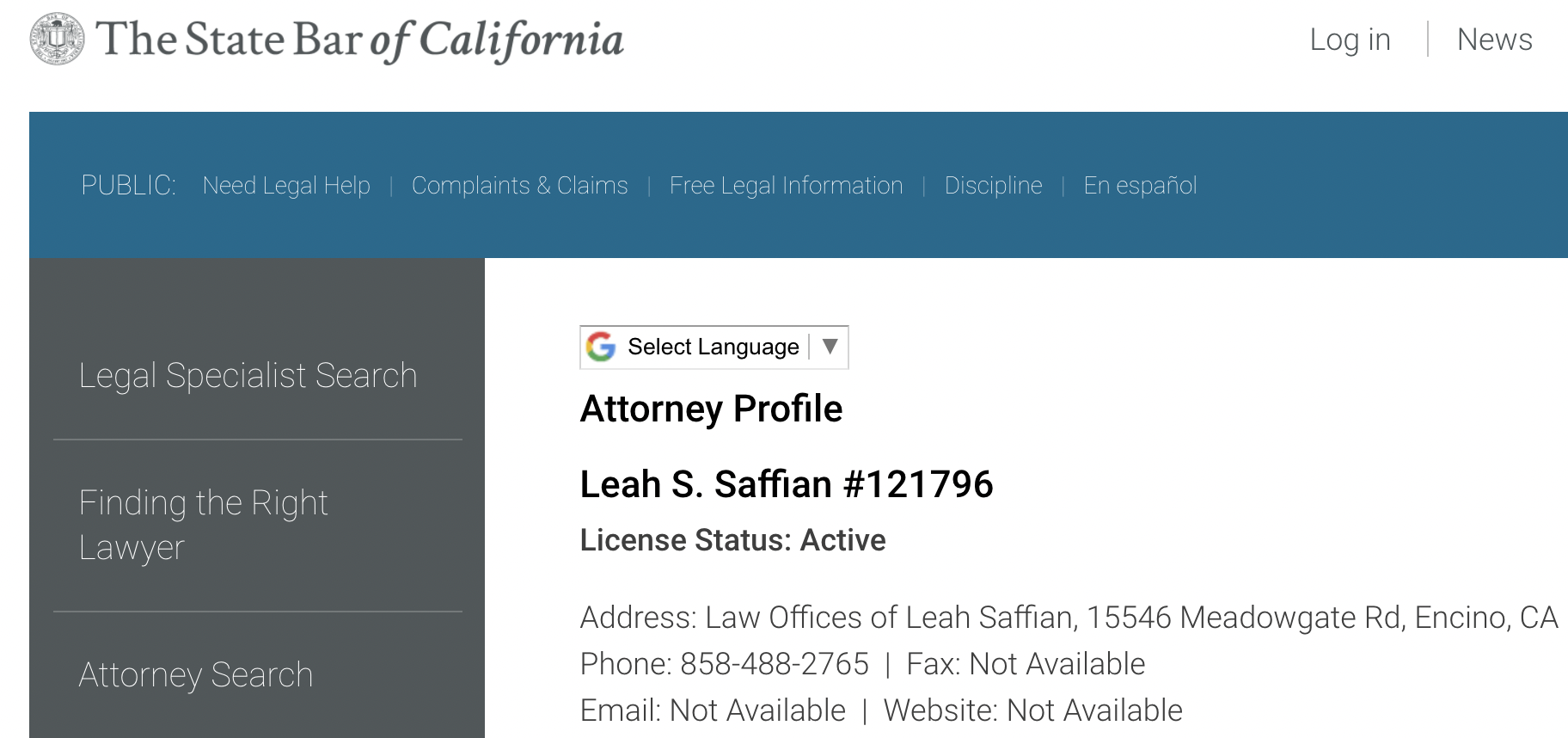
After that, I uploaded the photo into an EXIF data reader and found that the metadata was tagged with the word “Meadowgate.” A quick Google search of the words “Meadowgate” and “California” pulled up the full name Meadowgate Media Investments Inc, which was listed on a number of public records. I was able to look through public records and determine that the owner of Meadowgate Media Investments Inc is Leah Saffian. And that she was a practicing attorney in California.
Generally, you can find a lawyer’s license to practice through their respective state’s bar website, which is what I did. The State Bar of California website listed Saffain’s law office address, which was on Meadowgate Rd, Encino, CA.
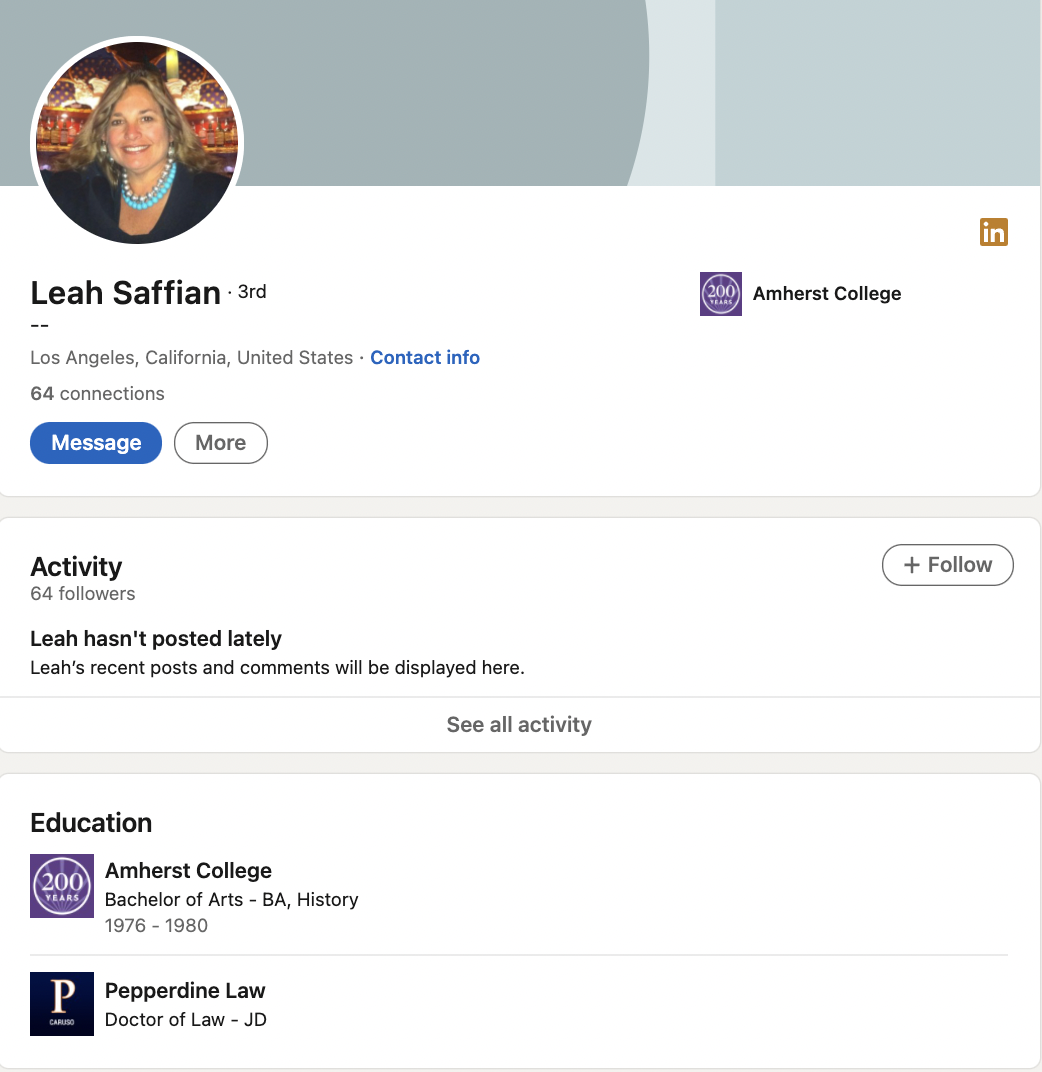
After I uncovered this information, I checked LinkedIn and found a possible page associated with Leah Saffian. From there, I discovered some social media postings on Instagram from Saffian that led me to believe she had close ties with Maxwell. It turned out she was Maxwell’s personal lawyer and friend.
Ultimately, my former NBC team and I were able to determine the photo was taken by Saffian, that it was altered, and was captured months prior.
How do I see EXIF data from social media?
So this is all well and good, but what happens if a source doesn’t initially send you a photo? What happens if the photo you’re investigating is from social media?
Well, chances are you have probably downloaded photos from Facebook, Instagram, and Twitter before. And if you have, it’s likely the EXIF data has been removed from those images. The reason for this is because when most photos are uploaded onto social media platforms like Facebook, Instagram, Twiter, and Pinterest, the photos are compressed, and the quality changes, thus also changing the photo’s format. When that happens, much or sometimes all the photo’s EXIF data is erased.
That generally means personal data is stripped out. And so is the copyright in the metadata, hence why it’s so easy for people to falsely claim they captured a photo on social media.
What websites store EXIF data?
The popular photo-sharing app, Flickr, keeps EXIF data on images. Generally, people looking at your photos on Flickr will be able to look up the EXIF data to learn about your camera, lens, aperture, and other settings you used to capture the photo. It also will contain the date you captured your photo, and sometimes the location.
If you want to remove EXIF data from your Flickr photos, you can do the following:
Click on the photo in Flickr and open it.
Below the photo, click Show/Hide EXIF.
Keep EXIF data secret
Users can also update their privacy settings to hide the EXIF data for all photos uploaded to their accounts.
Also, personal websites, company websites, and websites that generally host photos will likely have EXIF data. You can download the photo to your computer locally and then upload it to any of the resources I have listed above. I’ve used this method several times to track down sources for stories back when I used to be a journalist for news networks.
Case study Lev Parnas
For example, when prosecutors were investigating Lev Parnas, a Ukrainian-born American businessman who worked with Rudy Giuliani, who was accused at the time of violating federal campaign finance laws (he was since indicted), I was able to go onto Parnas’ consulting website and download photos from his website. From there, I look up the EXIF data for those photos. That information helped me determine when and where those photos were taken.
How do I remove EXIF data from photos?
Now, what if you want to remove EXIF data? Sometimes, when you’re looking through a photo, you might not find the EXIF data attached. More sophisticated users generally know how to erase metadata quickly. If you want to share photos, but you also want to make sure your EXIF data isn’t available, you can take these steps to remove it:
Use an image hosting site to wipe EXIF data
Image hosting site, Imgur, is a common photo hosting website that many users on Reddit frequent. You can also remove some EXIF data from your computer, which I think is generally an easy way of ensuring much of the critical EXIF data on your photos is erased if you are planning on hosting photos on a website or sharing them via email or text.
How to remove EXIF data on Windows
Select the image and right-click.
Select “Properties” and the “Details” tab.
Select “Remove Properties and Personal Information” at the bottom.
Select the options to remove in the next window and select OK.
On Windows, you cannot remove all EXIF data from the image but you have more control than you do on a Mac.
How to remove EXIF data on a Mac OS
Select the image and open it.
Select “Tools” and “Show Inspector.”
Select the “GPS” tab and “Remove Location Info” from the bottom.
Mac OS only allows you to remove location data from EXIF. To remove more you’re going to need an image editor.
As you can see, EXIF data can be powerful information to help you verify and determine whether a photo is real or not. If you liked this article, check out my other blog posts where I discuss how to verify videos and other tips for content creators. I also have a Youtube Channel where I upload a lot of skill-sharing tips and tutorials. Follow me there to keep learning and growing, and remember, stay curious.
How to investigate like a digital sleuth
The situation is intensifying between Russia and Ukraine. The latest news indicates that some journalists are being restricted from accessing areas in order to do their reporting.
Although I don’t work as a journalist with a news network currently, I think this is an important time to share some basic social newsgathering tips and skills with the public. Some of the tips and techniques I have in this article can, hopefully, help any journalist or citizen get the information they need to better understand whether something is real or not.
In this article, we’ll explore common ways to verify or debunk photos and videos using examples from January 2020.
How do you verify a photo?
Reverse image search is one of the best ways that you can easily check whether a photo is real or not. There are plenty of resources to help you determine the source of a photo. My favorite tool is TinEye, which is an image search and recognition website. The owners of the website state that they are experts in computer vision, pattern recognition, neural networks, and machine learning, which they use to help them decipher and analyze photos.
In January 2020, as tensions between the U.S. and Iran were increasing, Arizona Republican Congressman Paul Gosar posted a photo of former President Barack Obama shaking hands with the Iranian president. "The world is a better place without these guys in power," he tweeted.
But was the photo actually real?
I downloaded the photo Rep. Gosar shared on Twitter, it has since been deleted, and I uploaded the image to TinEye. Immediately, the website brought up similar images, only many of these images were of President Obama and former Indian Prime Minister Manmohan Singh. I was also able to compare the photos and see that the color of the flag was changed, along with Singh being removed from the photo and swapped with a falsified image of Rhouhani. It turns out the original, undoctored photo was taken in 2011, which I was able to verify through reporting from news wires that published the photo back in 2011, and also White House archived records.
Fun fact: If you ever want to explore or learn more about White House photos, it’s helpful to check out the National Archives Catalogue where most of United States’ presidents’ diplomatic meetings and visits are photographed and stored on the website.
You also use this reverse image Google Chrome extension called RevEye, which I find really handy because you can easily right-click an image and reverse image search. The Chrome extension allows you to search images against different search engines like Yandex (Russian), Bing (Microsoft), and TinEye. Sometimes, this can be handy because different search engines yield different results.
How do you verify a video?
This is a bit harder. The first step is to watch the video all the way through. Ask yourself these questions:
What am I seeing in this video?
What are the landmarks? For example, do I see buildings in the background?
Are there street signs? If so, what language are they in?
Do I hear anything? Anyone speaking? If so, what language? What are they saying?
What time of day is it? What is the weather like in this video? For example, is it rainy or sunny or snowy?
Back in early 2020, tensions between the U.S. and Iran were rising. Then reports emerged of a plane possibly exploding over Tehran. Soon after, this video started circulating on Telegram, an encrypted messaging app, claiming to show a passenger plane being shot down. Below is a short version of the original Telegram video.
Here’s how my former NBC team and I answered the following question:
What am I seeing in this video?
The video shows a flash of light in the sky above what looks like an area with white buildings or factories.
What are the landmarks? Do I see buildings in the background?
There are white buildings in the background. There appears to be a black, metal structure in the foreground, and possibly a fence.
Are there street signs? If so, what language are they in?
We don’t see any visible street signs.
Do I hear anything? Anyone speaking? If so, what language?
In the video, you hear a loud bang. And dogs barking after the bang.
What time of day is it? What is the weather like in this video? Is it rainy or sunny or snowy?
It’s not clear what the weather is like at this time. But it is nighttime.
Here’s what we know from official sources who spoke to NBC News or shared information publicly on verified social media channels:
Ukrainian passenger jet Flight PS752 went down after shortly departing Tehran Imam Khomeini International Airport in Iran.
Ukrainian Foreign Minister Vadym Prystaiko said in a public statement that 82 of the people on board were Iranian, 63 were Canadian and 11 were Ukrainian, including the nine crew members. Ten were from Sweden, four were from Afghanistan, three were from Germany and three were from the United Kingdom.
Western intelligence told reporters they believed a missile struck the plane
While leading my former team at NBC News, I was able to use visual clues from the video, and cross-check them against satellite imagery in order to identify the moment the plane was struck with an object in midair before crashing.
Here are the steps my former team and I took in order to verify this video:
Look up flight data: Every commercial airplane has a transponder, which gives information like a plane’s altitude and location to ATC. A transponder can help identify an airplane. It’s very hard, almost impossible, for a commercial plane to just disappear. That’s why the disappearance of Malaysia Airlines flight MH370 was so troubling, because its transponder signal disappeared, and thus, so did the plane. Websites like Flight Aware and Flight Radar 24 can help you find planes based on information like flight number, location, and time of flight.
In order to verify whether the explosion in the Telegram video was actually of a plane, we first needed to determine when Flight PS752 was scheduled to take off from Imam Khomeini airport. Using Flight Radar we were able to locate the flight’s path, which shows that it was actively flying in the air for a short period of time after taking off from Imam Khomeini airport at night. This helps us know two things about the plane: It took off during the nighttime, so the sky was dark. And it was in the air for only a short amount of time, according to flight data from the transponder.
You can see that flight map below:
Satellite imagery: Next, we used Google Earth to look at the surrounding area near the Imam Khomeini airport, which is known as Parand, a planned city in Robat Karim County. We determined that we needed to look at Parand based on the flight path data.
Although we knew we needed to look at the region of Parand, we needed more help identifying where exactly to look because it is still a city with an area of 5.664 mi², therefore, we looked back at the Telegram video to see if we can find any visual clues. Remember we noticed those white buildings in the background? Well, if you zoom into Parand on Google Earth, you can see that there are a few places in the city where the building architecture looks very similar.
We went back to Google Earth and zoomed in closer to the city until we found a set of buildings that appeared to match the buildings in the Telegram video. We also noticed that this set of buildings had black metal structures nearby that looked similar to the ones in the video. Considering the flight information, and where directionally the plane was flying from, we were able to determine the approximate location of where the video was captured.
This helped us verify that the video did show footage from Parand. We found another video that was similar to this one, only we could hear someone in the video say the word “Ferdosiye," which is a city about 22 miles from Parand. And the debris of the plane was found in Khalajabad, the following morning, which is relatively close to both locations.
That’s how we were able to verify the Telegram video, which shows the moment a missile struck Flight PS752.
Applying social newsgathering techniques to verify Russia-Ukraine tensions
These two case studies are good exercises you can use to help prepare you if you’re hoping to learn more about the situation between Russia and Ukraine, or if you’re interested in learning more about other newsworthy events. For example, videos below surfaced in February 2022 on TikTok, allegedly showing Russian tanks (National Guard) heading towards the Ukrainian border.
Satellite imagery from Maxar Technologies (Maxar also provides satellite imagery to Google Earth, and publishes their findings on their public social media channels and sends them to news organizations) shows Russia amassing troops near Ukraine's borders.
TikTok videos have also emerged showing men dressed in military uniforms that look similar to Russian military uniforms. The video below shows some of these men gathering at a train station in Buynaksk, which is located in Russia’s southwestern Dagestan region. You can compare the building architecture at the train station to what is documented on Google Maps, Google Reviews, and Google Image Search. In addition, you can crosscheck this video with other photos of the train station that were published publically on social media accounts to help verify the location. As for the uniforms, you can also check the pattern and uniform style of the troops by taking a screenshot of the video and uploading it to TinEye. This reserve image search technique, which you can sometimes use even with a video thumbnail, can help you find similar images or identify patterns.
As you can see, we’ve applied some similar principles and techniques to the Russia-Ukraine TikToks as we did with the Iran case studies above. Investigating like a digital sleuth by using social newsgathering skills takes time and practice. But it’s important to keep in mind that the best investigators are persistent, skeptical, thorough, and think critically.
In the upcoming weeks, I’ll be publishing more content around how to conduct social newsgathering investigations. In the meantime, stay curious.