How to find EXIF data
When you want to learn more about a photo, sometimes reverse image search might not be enough information to determine the full story of the photo you’re investigating. If you want more information about the location of a photo, the time it was captured, and the make and model of the camera that captured the image – then you’re going to need to dive into the photo’s EXIF data (exchangeable image file).
Why does EXIF data exist?
Although EXIF data may seem spooky to some, or an invasion of privacy to others, it’s actually pretty useful information. For example, have you ever looked at your iPhone and it displays a photo that you captured on a specific day or location and it automatically creates an album for you? Well, if you think about it, you likely didn’t have to manually enter that information for each photo on your phone, right? That’s because EXIF data allows photo-storage programs and services to organize your photos based on date and location, which can make it easier for you to find photos on your computer or phone.
When you share that original photo via email or upload it to certain websites or platforms, the photo’s EXIF data will be attached to it. Many digital security experts believe it is good for consumers to know about EXIF data when they share their photos because consumers may be unaware that they are sharing way more information than they may intend to do.
How do I look up a photo’s EXIF data?
There are a few ways to look up EXIF data, which I will show you in this article. I will also show you a case study for why this technique can really help you determine whether the photo you’re looking at really represents what someone claims it does.
When you take a photo, you’re not just capturing the world around you. You’re also capturing information like date, time, camera model, and other camera settings that are stored as metadata onto your photo. Even information like shutter speed and GPS location are recorded. You don’t need a lot of fancy software to look up this data.
If you’re on a web browser, the website EXIF data viewer is an easy way to upload a photo and look through its metadata. Be mindful of the image size you are looking up though. Web-based EXIF readers usually can’t handle high-resolution photos.
How to check EXIF data on Windows
You can also check EXIF data on your computer, which is my favorite way of doing it. On Windows computers, you just have to right-click on the photo that has been locally downloaded onto your computer and choose “Properties” in the Windows dialogue box. Once you select properties, navigate to “Details.” There, you will find all the camera information you’re looking for – the metadata (e.g. EXIF data).
How to check EXIF data on a Mac
If you’re using a Mac OS, you can also view EXIF data. Once you open a photo on your Mac, you will be in “Preview” mode. From there, click “Tools” in the menu bar. Then click “Show inspector.” This will open a new window where you can select “EXIF.” Here’s a visual breakdown below:
Step 1: Select your photo on your Mac and open it in “Preview”
Step 2: Navigate to “Tools” and select “Show Inspector”
Step 3: Go to “Exif”
Step 4: Based on the device settings of the camera you used to capture your original photo, you will be able to see a lot of information. As you can see here, this photo was captured on July 14, 2021 on an iPhone.
How can journalists use EXIF data for research?
Journalists, citizens, and digital sleuths can use EXIF data to help corroborate an eyewitness account. For example, if someone says they witnessed a stage collapse at a concert and they captured photos of the incident, you could ask them to send you the original photo they captured via text or email. From there, you can look up the EXIF data to see if the photo was really captured in the place, time, date, and with the camera, the eyewitness claims it was captured. This information can help confirm an eyewitness’ story.
Case study of Ghislaine Maxwell
You can also debunk a story or photo with the help of EXIF data. Take the case of Ghislaine Maxwell (who was convicted of sex trafficking in 2021), Jeffrey Epstein’s associate, who in 2019 appeared to be at an In-N-Out Burger soon after reports of Epstein’s death. When I was working at NBC, I got an email to our tips inbox which claimed that Maxwell was not running from the cops or impacted by Epstein’s death, but was instead enjoying her life in sunny California. I thought the email sounded really odd. And I noticed the tipster sent the email with an attached photo.
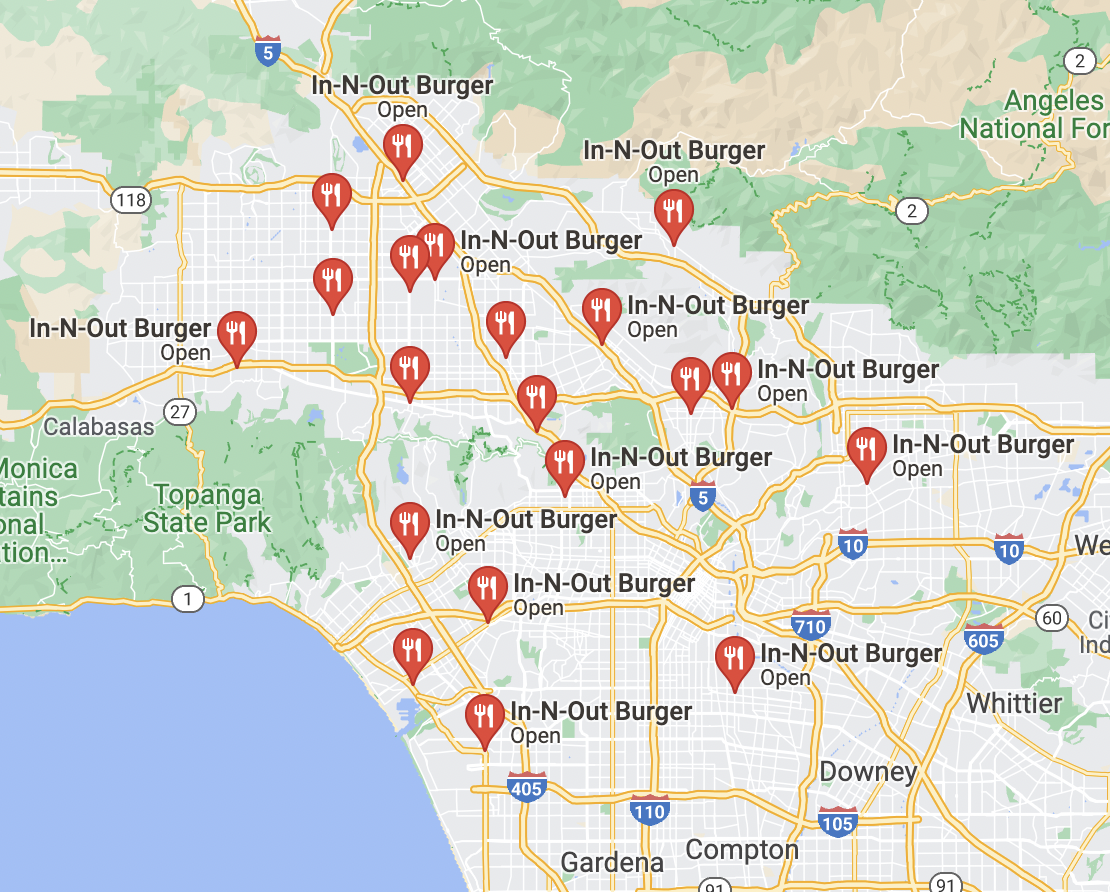
Before we even start looking at the EXIF data, I noticed the photo had a lot of information in it. We obviously know this is an In-N-Out Burger based on the signage. But where exactly is this restaurant located? Using clues like the buildings behind Maxwell, the billboard, and the bus stop we can make a determination about the exact location using Google Maps and Google Street View.
What’s distinctive in this photo in the background is the cannabis billboard. I’ve spent some time in California, so I have seen similar billboards near highways. There are also a lot of buildings clustered around the In-N-Out Burger, which makes me think this photo may have been taken near Los Angeles or in another dense California city area. When you look up all In-N-Out Burgers in Los Angeles in Google Maps, you see that there are about 12 locations.
The next part is a little tedious, but basically, I used Google Street view to look through all the locations until I found one that had the same cannabis billboard in the background. From there, I was able to figure out that the photo was taken at an In-N-Out Burger in Hollywood/Universal City. Not only did the billboard match, but there was also a bus stop and the buildings around the In-N-Out Burger that had green roofing, which matched the tipster’s photo.
So that’s how I was able to establish the location.
Fun fact about bus stops and billboards: Generally, you can call up the business that owns billboards and bus stops because that’s how they attract new clients who may want to advertise with them. When you look at the bus stop in the photo, you see a poster for “Good Boys,” which at the time my former team received this email, was premiering that weekend. The movie was a Universal movie, so my team was able to call the Universal marketing team to ask if the movie was being advertised at that bus stop location. The marketing PR team said no. Which meant that this photo was possibly altered.
Since we figured out the location of this In-N-Out Burger through Google Street View, my former team at NBC was able to figure out the business that owned the bus stop ad spot. We called the number and determined that there wasn’t a movie being advertised there. It was a healthcare ad for a hospital. It was likely then that the person who doctored this photo wanted us to believe it was captured recently by adding the movie poster to the photo.
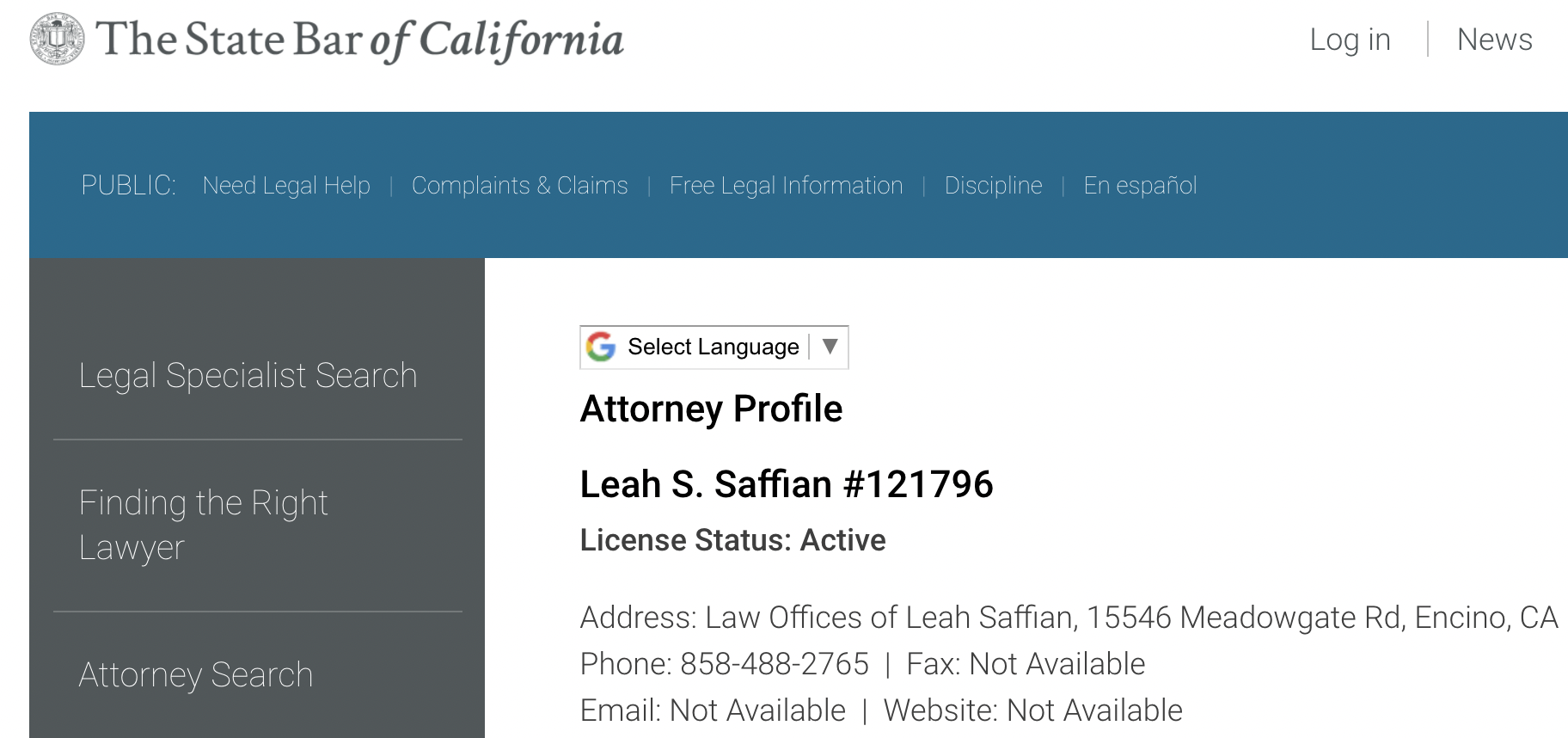
After that, I uploaded the photo into an EXIF data reader and found that the metadata was tagged with the word “Meadowgate.” A quick Google search of the words “Meadowgate” and “California” pulled up the full name Meadowgate Media Investments Inc, which was listed on a number of public records. I was able to look through public records and determine that the owner of Meadowgate Media Investments Inc is Leah Saffian. And that she was a practicing attorney in California.
Generally, you can find a lawyer’s license to practice through their respective state’s bar website, which is what I did. The State Bar of California website listed Saffain’s law office address, which was on Meadowgate Rd, Encino, CA.
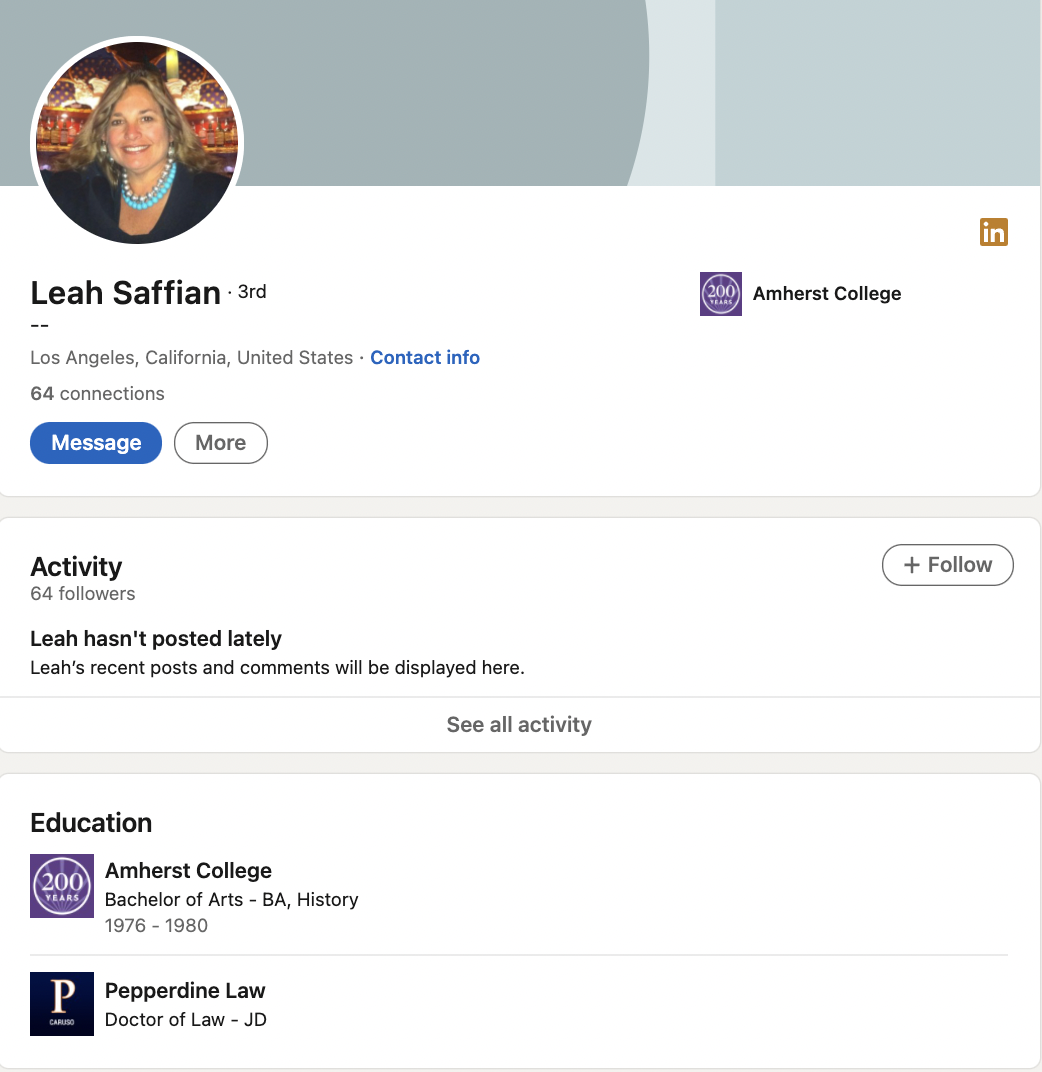
After I uncovered this information, I checked LinkedIn and found a possible page associated with Leah Saffian. From there, I discovered some social media postings on Instagram from Saffian that led me to believe she had close ties with Maxwell. It turned out she was Maxwell’s personal lawyer and friend.
Ultimately, my former NBC team and I were able to determine the photo was taken by Saffian, that it was altered, and was captured months prior.
How do I see EXIF data from social media?
So this is all well and good, but what happens if a source doesn’t initially send you a photo? What happens if the photo you’re investigating is from social media?
Well, chances are you have probably downloaded photos from Facebook, Instagram, and Twitter before. And if you have, it’s likely the EXIF data has been removed from those images. The reason for this is because when most photos are uploaded onto social media platforms like Facebook, Instagram, Twiter, and Pinterest, the photos are compressed, and the quality changes, thus also changing the photo’s format. When that happens, much or sometimes all the photo’s EXIF data is erased.
That generally means personal data is stripped out. And so is the copyright in the metadata, hence why it’s so easy for people to falsely claim they captured a photo on social media.
What websites store EXIF data?
The popular photo-sharing app, Flickr, keeps EXIF data on images. Generally, people looking at your photos on Flickr will be able to look up the EXIF data to learn about your camera, lens, aperture, and other settings you used to capture the photo. It also will contain the date you captured your photo, and sometimes the location.
If you want to remove EXIF data from your Flickr photos, you can do the following:
Click on the photo in Flickr and open it.
Below the photo, click Show/Hide EXIF.
Keep EXIF data secret
Users can also update their privacy settings to hide the EXIF data for all photos uploaded to their accounts.
Also, personal websites, company websites, and websites that generally host photos will likely have EXIF data. You can download the photo to your computer locally and then upload it to any of the resources I have listed above. I’ve used this method several times to track down sources for stories back when I used to be a journalist for news networks.
Case study Lev Parnas
For example, when prosecutors were investigating Lev Parnas, a Ukrainian-born American businessman who worked with Rudy Giuliani, who was accused at the time of violating federal campaign finance laws (he was since indicted), I was able to go onto Parnas’ consulting website and download photos from his website. From there, I look up the EXIF data for those photos. That information helped me determine when and where those photos were taken.
How do I remove EXIF data from photos?
Now, what if you want to remove EXIF data? Sometimes, when you’re looking through a photo, you might not find the EXIF data attached. More sophisticated users generally know how to erase metadata quickly. If you want to share photos, but you also want to make sure your EXIF data isn’t available, you can take these steps to remove it:
Use an image hosting site to wipe EXIF data
Image hosting site, Imgur, is a common photo hosting website that many users on Reddit frequent. You can also remove some EXIF data from your computer, which I think is generally an easy way of ensuring much of the critical EXIF data on your photos is erased if you are planning on hosting photos on a website or sharing them via email or text.
How to remove EXIF data on Windows
Select the image and right-click.
Select “Properties” and the “Details” tab.
Select “Remove Properties and Personal Information” at the bottom.
Select the options to remove in the next window and select OK.
On Windows, you cannot remove all EXIF data from the image but you have more control than you do on a Mac.
How to remove EXIF data on a Mac OS
Select the image and open it.
Select “Tools” and “Show Inspector.”
Select the “GPS” tab and “Remove Location Info” from the bottom.
Mac OS only allows you to remove location data from EXIF. To remove more you’re going to need an image editor.
As you can see, EXIF data can be powerful information to help you verify and determine whether a photo is real or not. If you liked this article, check out my other blog posts where I discuss how to verify videos and other tips for content creators. I also have a Youtube Channel where I upload a lot of skill-sharing tips and tutorials. Follow me there to keep learning and growing, and remember, stay curious.